An application to minimize memory footprint.
Minimem
The application can optimize the memory used. Some applications when run over a long time start hogging a lot of memory, this tools optimizes the memory usage and free it.
Mozilla is a good example of such a process (at least I was facing the issue) but is irreplaceable. :)
Tuesday, June 30, 2009
Tuesday, June 23, 2009
Pitfalls of SOA adoption
An old link about pitfalls of SOA adoption.
Pitfalls of SOA adoption - Thomas ErlMost of the points are still valid, specially the performance impact.
OWSM setup for signature verification
Purpose
Setup OWSM to perform signature validation
Prerequisites
- JKS store should be setup and ready to use. Refer to http://tech-sash.blogspot.com/2009/06/keystore-setup-for-owsm.html for more details.
- OWSM gateway is already created. To create refer http://download-uk.oracle.com/docs/cd/B31017_01/integrate.1013/b31007/gateways.htm
Steps
Step 1: Getting the wsdl URL for the service to be secured.
- Login to the BPEL console.
- Select the process to be secured and copy the wsdl url.
- Move to the WSDL tab.

- Remove the version from the wsdl location. http://server:port/orabpel/domain/BPELProcess1/1.1/BPELProcess1?wsdl to http://server:port/orabpel/domain/BPELProcess1/BPELProcess1?wsdl and copy the new wsdl url. This will ensure the OWSM is always pointing to the latest version of process deployed.
- Remove the version from the endpoint location. http://server:port/orabpel/domain/BPELProcess1/1.1 to http://server:port/orabpel/domain/BPELProcess1 and copy the new endpoint location. This will ensure the OWSM is always pointing to the latest version of process deployed.
To secure a java web service (or any other web service), get the correct web service wsdl URL.
Step 2: Register the web service in
OWSM.
- Login to OWSM.
- Go to PolicyManager --> Register Services. Click on Services.

- Click add new service.

- Insert the required details. Please note enter the correct wsdl URL from step 1.4 without the version and then click next.
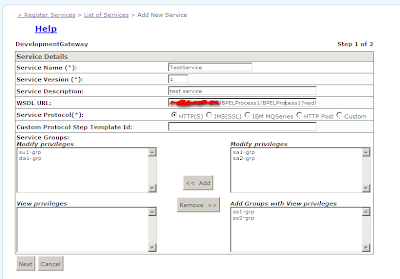
5. Click Finish and then commit.
6. Go back to RegisterSerices --> List Of Services, find the service created and click on edit.
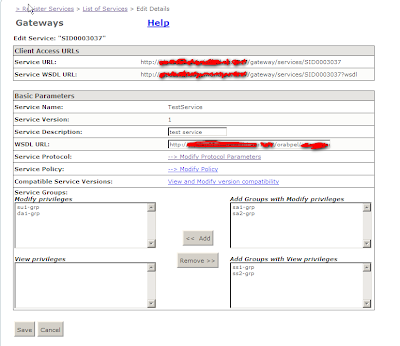
Note the Service URL and the Service Endpoint URL. These will be provided to the client and also used for testing.
7. Click on Modify Policy
8. In the Request pipeline, click on 'Add Step Below' in the Log step and click OK.
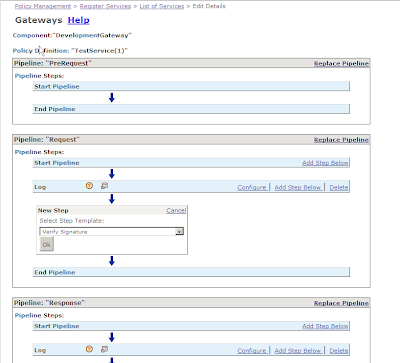 9. Click on configure in the VerifySignature step. Fill in the appropriate values. Use serverpass for the value while creating the keystore and the alias as the value while importing the client certificate.
9. Click on configure in the VerifySignature step. Fill in the appropriate values. Use serverpass for the value while creating the keystore and the alias as the value while importing the client certificate.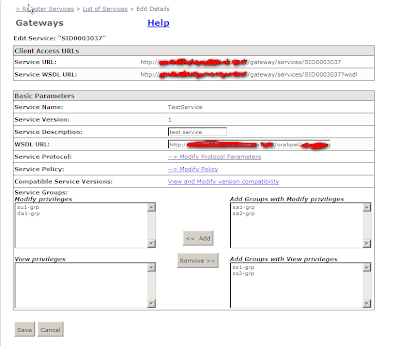 10. Click OK and the commit the changes. The update to the signature are done.
10. Click OK and the commit the changes. The update to the signature are done.
Keystore Setup for OWSM
Purpose
keytool -list -keystore [keystore-file.jks] -storepass [serverpass]
Set up the keystore to be used by Oracle Web Services Manager (OWSM) to perform digitial signature validation.
Prerequisites
The client's public key (.cer file) should be provided.
Steps
Step 1: Creating server store.
Use the java keytool command to create a keystore.
keytool -v -genkey -keyalg RSA -keysize 1024 -keystore [keystore-name.jks] -storepass [serverpass]-alias server1 -keypass [server]
Example server output:-
keytool -v -genkey -keyalg RSA -keysize 1024 -keystore server-store-1jks -storepass serverpass -alias server1 -keypass server
What is your first and last name?
[Unknown]: SashCo
What is the name of your organizational unit?
[Unknown]: DPP
What is the name of your organization?
[Unknown]: SashWorld
What is the name of your City or Locality?
[Unknown]: Dubai
What is the name of your State or Province?
[Unknown]: Dubai
What is the two-letter country code for this unit?
[Unknown]: AE
Is CN= SashCo, OU=DPP, O= SashWorld, L=Dubai, ST=Dubai, C=AE correct?
[no]: Y
Generating 1,024 bit RSA key pair and self-signed certificate (MD5WithRSA)
for: CN= SashCo, OU=DPP, O= SashWorld, L=Dubai, ST=Dubai, C=AE
[Storing server-store-1jks]
Step 2
Add the provided public key to the java keystore.
keytool -import -noprompt -trustcacerts -keystore [keystore-file.jks] -storepass [serverpass] -alias [alias] -file [certificate-file.cer]
Example server output:-
keytool -import -noprompt -trustcacerts -keystore server-store-1.jks -storepass serverpass -alias sashwat -file sashwat.cer
Certificate was added to keystore
Step 3:
Use the following command to list the certificates in the .jks file
keytool -list -keystore -storepass
Acronym / Abbreviation
OWSM - Oracle Web Services Manager
keystore-name.jks - Name of the new java keystore
serverpass - password of the keystore
keypass - password of the private key
clientalias - alias for the client
certificate-file.cer - the certificate file provided by client
Helpful Links:-
Java keytool reference :-
Tuesday, June 16, 2009
A very nice regular expression tool
This a very useful regular expression verification tool.
Regex Coach
I haven't tried many but never needed to look further.
Regex Coach
I haven't tried many but never needed to look further.
Subscribe to:
Posts (Atom)